When building a platform that calculates and defends legal deadlines, every improvement matters. This week, I focused on strengthening the backend—making calculators more flexible, audit trails more robust, and narrative output more defensible.
Here’s what changed, and why it matters.
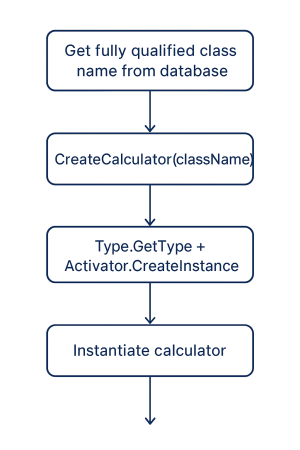
🔧 Flexible, Modular Calculators
Calculators now handle the full lifecycle of legal deadline computation, including edge cases like discovery rules, minor tolling, and statutes of repose. They’re designed to adapt to different jurisdictions and case types without changing the core engine.
Why it matters: This modularity allows the platform to scale efficiently while maintaining consistency and reliability. Testing, auditing, and client-specific adjustments are easier and safer.
🗃️ Robust Audit Trails
Every calculation now generates a persistent, queryable audit trail. This ensures that all decisions are traceable, making outcomes defensible and transparent for both internal review and client reporting.
Why it matters: Lawyers and firms can rely on the platform to document how deadlines were calculated, reducing risk and providing clear evidence if questions arise.
🧾 Explicit Handling of Discovery Logic
The system now formally incorporates discovery rules, ensuring that all relevant legal considerations are applied consistently. This is critical for cases where the timing of claim awareness affects the outcome.
Why it matters: Explicit handling of discovery logic reduces ambiguity and ensures defensible, consistent results for even the most nuanced cases.
🧠 Narrative-Ready Output
Each calculation produces structured outputs that can be transformed into client-facing explanations. Users get not only the deadlines but also clear reasoning behind them.
Why it matters: Providing understandable narratives helps lawyers communicate confidently with clients and supports decision-making grounded in defensible logic.
🧪 Comprehensive Testing
Unit tests cover a wide range of scenarios, including edge cases, constraint enforcement, and consistency checks.
Lesson learned: Strong automated testing safeguards both the integrity of calculations and the reliability of audit trails.
🧭 Final Thought
This week’s backend work may not be flashy, but it’s foundational. The system now guarantees that:
- Calculators are flexible and jurisdiction-aware
- Audit trails are persistent and transparent
- Legal logic is applied consistently and defensibly
- Outputs can be translated into clear, client-ready narratives
In legal tech, the difference between “working” and “defensible” is everything. This backend doesn’t just calculate — it remembers, explains, and protects.
About the Author
My name is Paul A. Jones Jr., and I am a software engineer and legal tech founder developing tools for professionals in law and other regulated industries. I write about systems thinking, modern workflows, and SaaS applications at PaulJonesSoftware.com. Follow me on Twitter: @PaulAJonesJr.
🔗 Related Posts
- Understanding Legal Deadlines: From Case to Audit Trail – A deeper dive into how deadlines are calculated and why audit trails matter.
- When Rules Collide: Designing a Class to Break Legal Deadline Ties – Learn how our software determines the winning rule: occurrence, discovery, repose, and others.